Microsoft Entra ID (formerly Azure AD Identity Protection) offers a comprehensive set of risk detection mechanisms designed to identify and mitigate potential security threats. These detections are crucial for organizations aiming to protect their identity infrastructure from various attack vectors. Below, we’ll explore the key aspects of risk detections in Microsoft Entra ID, highlighting how they function and how they can be effectively managed.
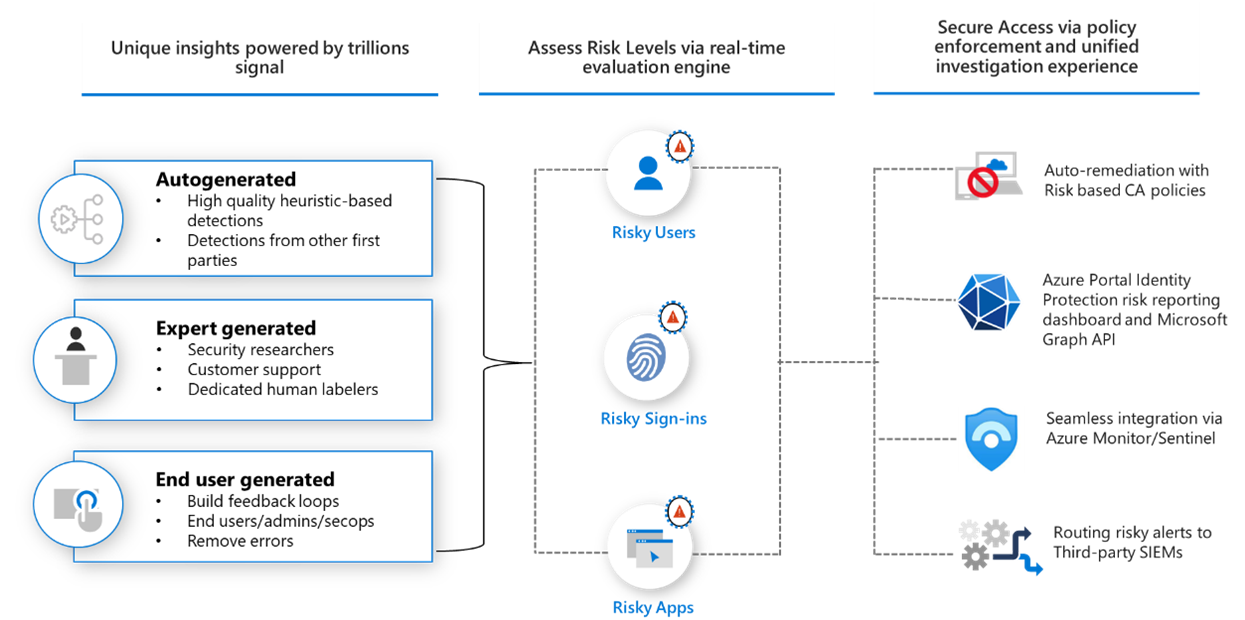
Types of Risk Detections
-
Atypical Travel: This detection identifies two sign-ins from geographically distant locations within a timeframe that would make it impossible for the user to physically travel between them. It’s particularly useful for catching potential credential sharing or hijacking incidents.
-
Impossible Travel: Similar to atypical travel, this detection flags sign-ins from distant locations that occur too quickly for normal travel, indicating potential unauthorized access.
-
Malicious IP Address: Sign-ins from known malicious IP addresses are flagged. These IP addresses are identified through various threat intelligence sources, including high failure rates of sign-ins from those IPs.
-
Password Spray: This detection identifies attempts to access multiple accounts using common passwords. A successful attempt triggers this detection, signaling a potential breach through credential stuffing.
-
Unfamiliar Sign-in Properties: If a sign-in occurs from a device, location, or IP address that is inconsistent with the user’s typical behavior, this detection is triggered. This helps catch scenarios where an attacker might have gained access to a user’s credentials.
-
Suspicious Inbox Manipulation Rules: Detected when unusual inbox rules are created, such as forwarding all emails to an external address, potentially indicating a compromised account being used for data exfiltration.
-
Attacker in the Middle: This high-precision detection occurs when an attacker intercepts credentials or tokens via a malicious reverse proxy during authentication. It’s a sophisticated attack that could lead to complete account takeover if not mitigated swiftly.
Managing and Responding to Risk Detections
To effectively manage these risks, Microsoft Entra ID provides several tools and practices:
-
Risk-Based Conditional Access: Organizations can create Conditional Access policies based on user and sign-in risk levels. For example, users detected with high risk might be required to complete multifactor authentication (MFA) or change their password before gaining access. These policies can be configured to automatically respond to risk detections, reducing the window of opportunity for attackers.
-
Risk Remediation: Once a risk is detected, remediation steps such as forcing a password reset or blocking access until the risk is addressed can be automatically applied. This helps in reducing the mean time to remediate, ensuring that risks are handled promptly.
-
User and Sign-In Risk Reports: Detailed reports are available that allow administrators to investigate risky sign-ins and user behaviors. These reports can be filtered by various parameters, such as risk level and detection type, to provide insights into potential security issues and guide remediation efforts.
-
Notifications and Alerts: Administrators can configure alerts to be notified of risky users or sign-ins. These alerts can be tailored to trigger based on specific risk thresholds, ensuring that critical issues are brought to attention in a timely manner.
Best Practices
-
Enable MFA for All Users: Ensuring that all users are registered for MFA significantly reduces the risk of unauthorized access, especially when used in conjunction with Conditional Access policies.
-
Regular Monitoring and Investigation: Regularly review risk reports and investigate any anomalies. Use tools like Microsoft 365 Defender to correlate identity risks with other security events across your environment.
-
Educate Users: Regularly inform users about the importance of secure sign-in practices and how to recognize suspicious activity. This can help in early detection and reporting of potential security issues.
In conclusion, Microsoft Entra ID provides a robust framework for detecting and responding to identity-related risks. By leveraging these tools and following best practices, organizations can enhance their security posture and protect against the growing number of cyber threats targeting user identities..